Oracle Cloud
Security Services
Design an automated Security Ops framework on Oracle Cloud with advanced intelligence, threat analytics, and predictive protection
Onboard the Oracle Artillery for Enterprise Security: High Performance and Seamlessly Scalable across multiple environments and hybrid landscapes
A key contributor to increasing threat management worries could be the underlying complex IT ecosystems: Over-abundant legacy assets, non-synchronous third-party systems, non-efficient hybrid and multi-cloud networks. In short, businesses leap forward and integrate whatever best IT solutions available for a certain vertical, but often falls short on the big vision: is the entire IT landscape, sporadically scattered across multiple regions and departments resilient enough against the most vicious cyberthreats and continuity risks?
Well a cloud tailored to address hybrid and multi-cloud scenarios could be an ideal answer. Hence, investing in Oracle Cloud Infrastructure would be a best fit, especially when it comes to orchestrating a universal cybersecurity strategy across the IT stack. Gain virtual assets on the cloud with complete control and unmatched security. It empowers enterprises with high-performance, secure, and highly available services to manage a wide variety of enterprise workloads. Over 40,000 Oracle customers have now moved out of their respective high alert cyber risk zones.
Want to learn how to keep cybercriminals at bay? Download our Oracle security brochure
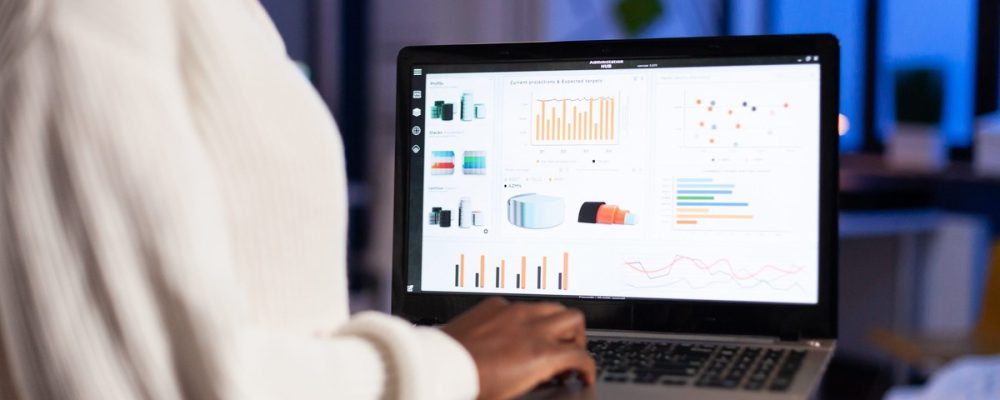
Cybersecurity on the Oracle Cloud Infrastructure: Maximum Protection, Maximized ROI

Visibility and Managed Service
Scale operations securely with super visibility and control on OCI – built with the highest privacy and security standards. Gain centralized OCI managed cybersecurity services or OCI cybersecurity-as-a-service and risk management visibility over your IaaS, PaaS, SaaS, CaaS environments. Avail automated alerting for any internal-external risks. Leverage OCI Cloud Guard to gain a universal security visibility across all Oracle tenants. Monitor, recognize, and remediate threats with ease. Deploy Identity Cloud Service to manage user access across all Oracle, non-Oracle, other cloud, and non-prem workloads.

Environment Complexity
Avail flexible, highly scalable, and agile security platforms and solutions on Oracle Cloud catering to any IT environment or resources, software, backend, workload, applications, networks, edge and IoT environments, and more. Leverage Oracle Cloud Guard, Identity and Access Management, Identity Cloud Service, Vault, Bastion, Web Application Firewall, and more.

Platform Reliability
Enjoy breakthrough reliability via integration of advanced information security and computing solutions on the Oracle Cloud. Adhere to modernized security frameworks and policies and protect your business with ease. Identify and manage threats anywhere with Cloud Guard, deploy configurable firewalls with Web Application Firewall, manage user access through IAM, manage encryption keys with Vault, and keep secure all databases across the system with Data Safe.

Costs
Eliminate the need for dedicated hardware and IT infra to handle security and risk management queries. With all IT assets secured on the Oracle cloud, reduce administrative overheads and pay for only what you utilize. Continuously audit OCI resources to optimize future compliance, risk assessment mishaps, and costs. Avail fast, cost-effective, and automated Disaster Recovery with Oracle Site Guard, Oracle GoldenGate, Oracle Recovery Manager

Compliance
Compliant-ready Oracle cloud security architecture including local, national, and global compliance-regulatory standards. Utilize Compliance Advisories for information and technical recommendations and controls, Compliance Attestations for independent assessment of third-party security and compliance controls, Compliance Documents Service, Corporate Security to manage and overview protection of enterprise assets, and Privacy for data privacy on cloud.

Resource Management
Automated Oracle cloud security services and solutions for constant monitoring, proactive maintenance, and risk alerting reduce the need for dedicated manhours. Administer global organizational security with ease and next to nil manual interventions for redundant tasks. Avail IAM and Identity Cloud Service to manage user access across ecosystems, Cloud Access Security Broker to gain threat visibility across the entire cloud stack with ease.

Incident Management
Significantly reduce mean time to detection and mean time to repair with Advanced Managed Detection and Response on Oracle cloud. Leverage Vulnerability Scanning to look for any loopholes across the IT stack, Cloud Access Security Broker to gain unprecedented threat visibility.

Access Control
Assess security and architecture access roles along with the entire organization with ease on OCI. Leverage the intuitive AWS Incident and Access Management (IAM), Cloud Identity Service, Bastion for restricted private access to hosted resources, and Privileged User Access Management (PAM) to assign definite roles and administer functionalities across the security workflows.

Outdated Policies
Move over from outdated cybersecurity policies. With IT assets on the Oracle cloud, embrace world-class methodologies, solutions, and frameworks: SIEM-SOAR, MITRE ATT&CK, CIS Security Controls, Zero Trust, etc. Leverage advanced Oracle native tools and compliance controls such as Compliance Advisories, Compliance Attestations, Corporate Security, Privacy for maximum impact.
Asset Monitoring and Protections
Gain 24/7 monitoring on your devices, data, networks, platforms, applications, VMs or virtual systems, servers, etc on OCI. Achieve unprecedented security over your entire backend and endpoint architectures. Track assets with embedded alerts, AM-ML-Behaviour Analytics, Oracle cloud-native cybersecurity tools such as Cloud Guard. Amp up threat management with Oracle Cloud Access Security Broker. Centrally manage keys and encryptions with Vault, restricted private access with Bastion, and firewall configurations with Web Application Firewall

Support and Governance
The dedicated Oracle Cloud Security Operations Centre (SOC) team adheres to all your cybersecurity monitoring, management, governance woes 24/7. Leverage one of the largest ecosystems of security partners, solutions with Oracle.

AI Capabilities
Integrate advanced threat intelligence powered by industry-leading platforms such as Microsoft, OSINT, STI&TAXI, MISP, etc. With advanced AWS security services capabilities, adopt smart threat hunting, deep cybersecurity analytics, predictive alerting, and preventive maintenance through proprietary AI-driven automation solutions.
Eager to renovate your cybersecurity architecture on the Oracle Cloud? Connect with our Oracle Cloud Security Experts today
CloudEngin and Oracle: Big Ideas and Big Evolutions
2021 witnesses a momentum towards Oracle Cloud as enterprises switch to new-age ERP for its significant competitive advantage and enhanced experience. To ensure a seamless transformation for enterprises through the right partnership. Oracle recognizes partners who demonstrate the specific expertise required to succeed. CloudEngin, with its full stack Oracle transformation suite and proven delivery excellence. has earned the prestigious Cloud Sell and Cloud Service Expertise and become a trusted global Oracle Cloud Transformation Partner recognized by Oracle. Read on to learn how CloudEngin earned its Oracle Cloud Sell and Cloud Service Expertise

Security Assessment of Oracle Workloads
CloudEngin is the trusted MSSP to thousands of enterprises across the globe, augmenting cloud migration, modernization, and management journeys from infra till application login layer end-to-end. As a trusted Oracle partner and part of our Oracle Security services, we offer a customized security assessment of Oracle workloads. This allows the development of a fail-proof smart security blueprint on the Oracle cloud that’s scalable at length, across all ecosystems and platforms.
- Align CAF for Security and Compliances requirements
- Understand the industry-specific compliances required for the organization
- Discover the current compliance control mapping
- Identify gaps in current compliance control and prepare check list
- Gain high-level assessment of cloud governance
- Get CAF-based security recommendations
Fail-proof. Threat-Resilient. Automated: OCI Security Cloud Adoption Framework (CAF)
Enterprises must clearly chalk out their security objectives and existing loopholes from all perspectives, including directive, preventive, detective and responsive aspects. Each of these perspectives has its own significance. Enterprises must build a comprehensive view of their security needs covering all possible scenarios to ensure maximum protection at all times.
Detective
Oracle Account Governance
GRC Control Framework
Control Ownership (OCI Shared Responsibility Model)
Data Classification
Change and Asset Management
Data Locality
IAM and Least Privileged Access
Security Operations Playbook and Runbooks
Preventive
Identity and Access
Infrastructure Protection
Data Protection
Detective
Logging and Monitoring
Security Testing
Asset Inventory
Change Detection
Responisve
Incident Response
Security Incident Response Simulations
Forensics
Want to safeguard your IT landscape for peak performance on the Oracle Cloud?
CloudEngin End-to-end Oracle Cloud Security Solutions and Services
CloudEngin advanced MDR and XDR solution and services on Oracle cloud deliver 360-degree protection, smart automating 24/7 real-time monitoring, threat hunting/risk prediction alerting, threat detection, and risk mediation. Gain deeper vigilance of your infra assets including data, networks, workloads, traffic, devices with ease and avail end-to-end response management: Threat and Mal Containment, Incident Analysis, Data Exploration, Response Orchestration. Secure your end-point connectivity with AI-powered End-Point Protection and Response Platform powered by Oracle cloud.
- Network Traffic Analysis
- Real-time Monitoring and Protection of Assets on AWS: Hosts infra, web applications, apps, devices, servers, Virtual solutions, Databases, Storage infra, cloud platforms, integrated third-party systems
- Endpoint Detection and Response on AWS
- Threat Hunting, Threat Investigation and Verification
- Threat Research and Intelligence
- AI/ML, Data-powered User Behaviour Analytics
- Data Protection and Forensics
- Database Activity Monitoring (DAM)
- MITRE ATT&CK Mapping
- Incident Containment, Analysis, Management
- OCI native Security with Multi-cloud Support
- Centralized Remote Response
Avail end-to-end cloud managed cybersecurity services or cybersecurity as a service on Oracle cloud. CloudEngin provides comprehensive cloud security strategy, blueprinting, POC, and implementation services for the Oracle Cloud including hybrid multi-cloud security management. Experience complete protection of your enterprise IT assets including networks, data centers, dataflows, workloads, computing devices, storage solutions, software, platforms, applications, edge networks, IoT environments on OCI.
- OCI Security Services: Strategy and Blueprinting Services
- Compliant AWS Security Services Offerings
- PaaS Security – Runtime protection, vulnerability management, Automatic configuration of security policies, network protection, secure endpoint
- IaaS Security – Automated auditing and monitoring, Identity Access Management, Data and Infra protection, Vulnerability Management and File Integrity Monitoring, Micro-Segmentation, Automated Compliance Monitoring
- CaaS Security – Managed Kubernetes security, container workload security management, CI/CD Scanning, Container-to-container micro-segmentation, Access Controls, incident response, forensic analysis
- SaaS Security – Network, platforms, systems, monitoring, and protection including firewalls, servers, emails, web applications
- Cloud Workload Protection Platforms (CWPP) – VMs, Hosts, IaaS, PaaS, CaaS, SaaS, data
- Cloud Security Posture Management (CSPM) – Multi-cloud security posture, Asset Inventory Management, Misconfiguration Monitoring, and Remediation, Compliance Monitoring and Reporting
- Cloud Access Security Broker (CASB) – Overall visibility, Threat Protection, Data Security, Access Control Management
- Hybrid/Multi-cloud managed security services
Having an in-house, dedicated cybersecurity services monitoring and response team could be a huge expense for any organization. This not only deters cyber threat monitoring, detection, and remediation but also limits the organization’s competency to adopt advanced security solutions and services. As an OCI-managed SOC (Security Operations Center) services provider, Cloud4C acts as an extended Cybersecurity Incident and Response Team (CSIRT) to your security management on Oracle cloud. The arrangement delivers the entire monitoring and threat management work with ease and assists your organization in the adoption of breakthrough cybersecurity frameworks, methodologies, and intelligent solutions backed on the Oracle cloud.
- SIEM-SOAR
- Reliable Security Engineering on GCP Expertise
- Identity and Access Management and Privileged Access Management (PAM)
- Advanced Threat Protection (ATP)
- Assets Security Management: Data, Host, Networks, Apps, Virtualization, Emails, Workloads, Workflows
- 24/7 Monitoring and Threat Response
- Centralized security management console
- Incident Recovery and Remediation
- Log Collection and Management
- Root Cause Analysis
- Vulnerability Assessment, Management, and Preventive Maintenance
- AI-powered Cybersecurity Solutions on GCP
- Alert Management
- Response Orchestration and Automation
- Compliance Audits and Management
- Reporting and Dashboarding
- Advanced Penetration Testing
Modernization of backend infrastructure plays a considerable role in improving frontend experiences. However, preserving the security of all IaaS solutions including virtual networks, computing, storage, have, and more is paramount to seamless business continuity. Shift and secure your networks, datacenter assets including databases, compute, storage, and servers infra onto dedicated AWS cloud solutions. Leverage special Oracle cloud-native applications, embrace virtualized infra to gain unprecedented agility and scalability of adopted enterprise applications without compromising asset security. Remove all backend physical infra hassles and pay for only what’s utilized.
- Automated auditing and monitoring
- Identity Access Management
- Data and Infra protection
- Vulnerability Management and File Integrity Monitoring
- Micro-Segmentation
- Automated Compliance Monitoring
With enterprises now increasingly opting for complex, multi-hybrid-private cloud IT environments, the universality of applications gets hampered. Businesses often fall prey to standalone systems and applications that work well for one backend platform or vertical but don’t function for another adopted cloud environment for a different vertical. This leads to the non-synchronicity of operations and hence catastrophic risk possibilities that could be solved using a pay-as-you-use secure Oracle Cloud PaaS platform. In addition to virtualizing and modernizing all core infra assets on the cloud, transition middleware, OS, architectures, protocols, APIs, libraries, Microservice modules, containers on OCI with utmost protection and zero disruptions. Leverage existing cloud-native platforms and OCI security architectures to develop, deploy, and run applications anywhere across any IT environment with maximum protection.
- Runtime protection
- Vulnerability management
- Automatic configuration of security policies
- Network protection
- Secure endpoint environments including IoT, Edge networks
With enterprises now increasingly opting for complex, multi-hybrid-private cloud IT environments, the universality of applications gets hampered. Businesses often fall prey to standalone systems and applications that work well for one backend platform or vertical but don’t function for another adopted cloud environment for a different vertical. This leads to the non-synchronicity of operations and hence catastrophic risk possibilities that could be solved using a pay-as-you-use secure Oracle Cloud PaaS platform. In addition to virtualizing and modernizing all core infra assets on the cloud, transition middleware, OS, architectures, protocols, APIs, libraries, Microservice modules, containers on OCI with utmost protection and zero disruptions. Leverage existing cloud-native platforms and OCI security architectures to develop, deploy, and run applications anywhere across any IT environment with maximum protection.
- Application network monitoring and security
- Core platforms monitoring and protection
- Backend application systems monitoring and protection
- Analyze, govern, and manage firewalls, servers, emails, web applications
Application modernization on the cloud has transformed enterprise operations across key verticals such as CRM, workflow management, supply chain management, compliance checking, financial audits, productions and manufacturing, IT administration, and more. To seamlessly achieve the same and administer applications and databases monitoring across multiple IT landscapes with ease, modern application development solutions are imperative – microservices, containers, functions. With CaaS security on Oracle Cloud, gain cutting-edge protection over Docker or Kubernetes containers, streamline development workflow security, architecture scanning, access controls, and more.
- Managed Kubernetes security
- Container workload security management
- CI/CD Scanning
- Container-to-container micro-segmentation
- Access Controls
- Incident response
- Forensic analysis
CloudEngin ensures military-grade data security during migration with end-to-end pre-backup, secure data transport, end-to-end encryption, data integrity management, thorough testing, and vulnerability assessment, and proper access management functionalities. Add extra layers of security to your OCI Storage solutions including files, blocks, objects, databases, database management software, etc. With numerous OCI native tools, 40+ Security Controls, dedicated Security Operations Center managed services, and cybersecurity experts, gain end-to-end protection of all your data assets on Oracle Cloud: networks, servers, management systems, applications, databases, virtual platforms, and more. Leverage end-to-end encryption over all organizational dataflows and advanced managed detection services. Avail 24/7 Monitoring, Identity, and Access Management with dedicated cloud-native tools such as OCI IAM. Embed threat intelligence and move the needle further to predict, avoid risks even before they occur. Embrace game-changing preventive maintenance capabilities (Self-Healing Operations).
Complexity of organizational networks and connectivity infra has increased multifold over the years. Rapid digitalization has enabled organizations to fast scale up operations, embed variant systems and IT solutions, decentralize processes across multiple locations, develop private network architectures to stay connected 24/7, and deploy global remote workforces. Needless to mention, network assets are the foundations of such a corporate labyrinth, enabling firms to seamlessly operate each day without a hitch. Hence, real-time network security attention for IT systems, workflows, enterprise applications, web assets, and more is paramount. Achieve end-to-end network security and protection on Oracle cloud with ease.
Adoption of Hybrid and multicloud environments is fast increasing owing to clear-cut benefits, the flexibility of IT adoptions, enhanced anti-risk postures, and more. Shield your Oracle hybrid or multi-cloud architecture with advanced cloud-native solutions. Gain the benefits of on-prem reliability and world-class OCI security. Shift security and monitoring check reliably between private and public workloads, touchpoints, assets. Comply with data locality-residency laws, gain ultra-low latency, and experience an uninterrupted, consistent performance of hosted workloads, applications, and systems with utmost security. While leveraging the benefits of multiple standalone cloud solutions and platforms basis mission-critical business objectives, streamline the entire multicloud resource management on OCI thereby extending the latter’s ground-breaking security solutions suite across all adopted heterogeneous cloud IT environments.
The age-old notion of security being an overarching boundary to the software development lifecycle is now slowly getting blurred. With the development processes now getting more complicated and cyberthreats exponentially rising, it’s wiser to integrate continual security policies, processes, and technologies into the DevOps culture and workflows. CloudEngin ensures ‘Security by Design’ on the Oracle Cloud platform and helps embed security as a core discipline in the development and management of IT systems, tools, microservices, containers, automation, APIs, testing tools via the Amazon Cloud. Below is the CloudEngin DevSecOps overview:
- Address Security Objectives and Threat Modelling
- IDE Security Plug-ins
- SAST/DAST/IAST SCA
- Integration Testing
- Software Signing. Leverage AWS Single Sign-On for a seamless SSO service.
- Signature Verification and Defense Depth Measurement
- RASP UEBA/Network Monitoring Pen Test
- Security Orchestration, RASP/WAF Shielding Obfuscation
- Dev Consumable Correlated Vulnerability Analysis: IoC/STIX/TAXII
- Modified Incident Response Management
The threat of the dark web cannot be underestimated. Hackers, cyber-criminals usually attack organizational databases, platforms to retrieve sensitive data such as user information, business records and IDs, log-in info to different platforms, financial data, social security numbers, and more and sell them at maximum prices on the dark web. With CloudEngin Dark Web Monitoring and Protection Solutions powered by the OCI architecture, track your enterprise data and get immediate alerts if your organization’s information is found on such threatening online sites. Take immediate action and bolster your firm’s security, preventing further attempts along similar lines:
- Dark Web Scan: Scan through the dark web for stolen usernames, passwords, Social Security numbers, credit card numbers for sale. Enterprise will be notified if organization information is found on the dark web.
- Dark Web Monitoring: Dark web monitoring is a continued dark web scan. This helps you consistently monitor activity on the dark web on a larger scale. Receive immediate alerts from the dark web monitoring service if your information is found.
- Dark Web Protection: Identity theft, Prevent data loss, Activation, and transfer of malware management over the Dark Web
Avail strategic recommendations from CloudEngin to better monitor and manage your organizational security on-premise or on the Oracle cloud. Gain continuous monitoring of OCI assets, resources, and systems, readiness interviews and assessments workshops on the overall security postures, access control review and key management, incident response management policy reviews, compliance audits and reporting, technical implementation inputs for greater data protection, advisory services for networking-server-assets misconfiguration, and more. CloudEngines extensive Oracle cloud security services consulting, managed cybersecurity services, cybersecurity as a service offerings help better streamline and transform your organizational security at ease.
- Public Discovery Scanning Services
- Vulnerability Assessment Services
- Compliance audits and reporting
- Data classification and segmentation
- Assets (Databases, Networks, Host-based Security Systems, Virtualization) security review, monitoring, and misconfiguration management
- Web application security testing services
- PCI-DSS ASV Scanning
- Advanced Black Box Penetration Testing Services
- Malware-Ransomware Detection and Scanning
Compliance-related complications often result in major loopholes in an organization’s IT workflows. This might be an inviting proposition to cybercriminals. CloudEngin compliant-ready offerings on the Oracle cloud along with dedicated Quality Management and Security teams ensure client facilities are duly compliant with data localization-residency laws, national regulations, local compliances, and international certifications. CloudEngin augments your IT security to truly world-class standards. Embrace leading AWS native solutions for end-to-end compliance check and management. Compliance adherences, not limited to are:
- IRAP
- Bank Negara
- Central Bank of Oman
- SAMA
- FINMA
- UAE Compliances
- RBI
- MAS
- OJK
- GDPR
- CSA
- PCI-DSS
- HIPAA
- GXP
- FedRamp
- International Standards: ISO-27001, ISO-27017, ISO-27018, ISO-22301, ISO-20000, AICPA SOC, AICPA SOC2
Move over from traditional cybersecurity services and solutions and embrace AI-driven cybersecurity with ease for end-to-end asset management and monitoring on the AWS cloud including last-mile connectivity and end device protection. CloudEngin advanced security intelligence solutions powered by the Oracle cloud offer deep threat hunting, advanced data forensics, anomaly detection, and automated response management with ease. Consolidate cybersecurity management for IP/Domain Reputation, File Reputation, CWPP, CSPM, CASB, Phishing-malware-ransomware feeds, IT assets. Avail the proprietary Self Healing or Preventive Maintenance Platform (SHOP) to not only reduce Meantime to Detect and Meantime to Repair but do away with threats via advanced risk prediction and automated risk healing processes.
- Powered by Industry-leading platforms such as Microsoft, OSINT, STIX&TAXI, MIS
- Up-to-date threat intelligence consolidated from multiple sources
- Segregation based on customer industry and vertical for focused analysis
- Improves threat-hunting and forensic capabilities with contextual, actionable threat indicators
- Augment your security capability with our rigorous analysis by CloudEngin security Experts.
- Seamless integration with major TIP, SIEM, and SOAR
- Automated Threat Research and Analysis
- Last-mile data extraction and protection
- Automated Threat Prediction, Detection, Mitigation, and Preventive Maintenance (Self-Healing Operations)
Connect with our Oracle Cloud Security Experts for end-to-end protection of your IT stack, any size and any complexity
Be Security-Smart. Attend our Special OCI Security Workshop
Why Partner with CloudEngin for your Application Modernization Journey on Oracle Cloud?

Global leader in platform-based, automation-driven, application-centric managed services and cloud infrastructure
Serving 2500+ enterprises including 50+ Global Fortune 1000 Companies in 29 countries across Americas, Europe, Middle East, and APAC for 12+ years

Dedicated OCI Security Services Management expertise with 40+ Security Controls, 25 Centres of Excellence, 1600+ cloud experts
Pre-met compliance needs for local, national, and global compliance requirements including IRAP, GDPR, HIPAA, SAMA, CSA, GXP, and ISO Certifications
3200 UTMs, 13000 HBSS Instances Managed, 800000 Events Per Second
7 Security frameworks utilizing the MITRE ATT&CK, CIS Critical Security Controls, and more

Comprehensive 24×7 OCI Security monitoring and Management program
Automated Security Solutions and Oracle cloud native tools management for threat prediction, detection, and response: Advanced Managed Detection and Response Solutions (MDR)

Global expertise in OCI managed SOC (Security Operations Center) services and solutions with complementary AWS Security Assessment Workshops

Dedicated DevSecOps on Oracle cloud portfolio
Dedicated OCI Cybersecurity Consulting and Compliance Audit Reporting offerings
Advanced CloudEngin Cybersecurity Incident and Response (CSIRT) team dedicated to OCI Security Management
Threat Intelligence powered by Industry-leading platforms such as Microsoft, OSINT, STIX/TAXII, MISP, etc. and Cloud4C Threat experts
Considerable threat management expertise in securing large and complex environments and using advanced functionalities of leading industry tools as well as Cloud-Native OCI Security tools

Experience in deploying and managing robust SIEM on SOAR solutions – helping enterprises to proactively assess vulnerabilities and automate, accelerate incident response on the Oracle Cloud
Oracle Security - Frequently Asked Questions (FAQs)
What is Oracle Security?
Oracle Security is a process to safeguard the mission-critical workload of enterprises, with the industry-best approach for compute, network, and storage, along with hardware.
It also offers the required security services to protect the most business-critical workloads.
What are the pillars of Oracle Security?
The pillars of Oracle Security include Customer Isolation, Data Encryption, Security Controls, Visibility, Secure Hybrid Cloud, High Availability, Verifiable Secure Infrastructure
Begin or augment your cloud security journey today. Connect with our Oracle Cloud Security Experts
Schedule a consultation with our Cloud experts and get answers for any specific queries you may have. You can also schedule a visit to our Datacenters, or share feedback on our website and services.
