Explore the advantages of adopting Compliance-as-a-Service for Banks
Explore the promise of Azure Sentinel for advanced enterprise IT security
A dark yet insightful dive into the Ransomware world. Stay aware and beware
Cybersecurity on Cloud:
The Road to Invincibility
This is not about fear, a realization instead: Cybersecurity policies of most organizations are stunted. And, Cloud computing along with its solutions suite encapsulating Deep AI, Big Data, Automation have shown the much necessary ‘bullish silver lining’. As the world’s leading application-focused cloud managed services provider, CloudEngine suite of MDR, Managed SOC, ATP, Threat Intelligence, Security Automation, and Managed Compliance-as-a-Service offerings powered by cloud along with its multiple award-winning Self Healing Platform (SHOP) helps businesses streamline their entire IT stack end-to-end even from the most advanced threats, in a single SLA. Stay protected, stay future-ready.
With 2.1 million plus ‘detected’ phishing sites on the web, only 5% of the world’s information is protected
Cybercrimes to cost 10 trillion dollars to global enterprises by 2025

Maximum Protection at Maximized ROI:
Single Partner addressing End-to-end Security needs
Gain centralized managed cybersecurity services across the IT stack including on-prem, public, private, hybrid, or multi clouds.
Remain Compliant, Anytime Anywhere
Enjoy fully reliable, verified, and compliant-ready security solutions. Leverage Cloud Engine’s managed compliance services.
Stay Updated and Ahead of the Curve
Adhere to modern security frameworks like OODA, Zero Trust, MITRE ATT&CK, CIS Security Controls, etc.
Detect Fast. Respond Faster
Significantly reduce mean time to detection and mean time to repair with Advanced MDR. Embed AI-enabled threat hunting, automated response management.
Predictive and Preventive
Embrace Automation and AI- Integrate advanced threat intelligence powered by industry-leading platforms such as Microsoft, OSINT, STI&TAXI, MISP, etc. Adopt preventive maintenance.
Gain 24/7 Support
Dedicated Security Operations Centre (SOC) team adheres to all your cybersecurity monitoring, management, governance woes 24/7.
Cloud Engine End-to-end Cybersecurity Solutions and Services
Cybersecurity Consulting
Cybersecurity Assessment
Cybersecurity Strategy
Cybersecurity Governance
Audit and Reporting
Azure Sentinel Consulting
Managed Security Services
Public Cloud Managed Security
Cloud Native Security
Hybrid Multicloud Security
Public Cloud Security Solutions
Self Healing Platform
Zero Trust Security
Microsoft Zero Trust Security
Dark Web Protection
Advanced MDR
Endpoint Security
Incident Management
Threat Hunting
Threat Intelligence
Database Activity Monitoring
Data Forensics
DNS Security
Zero Day Attacks
Anti Phishing
MITRE ATT&CK
Standard Managed SOC (Security Operations Center)
Managed SOC Services
Data Security
Network Security Services
Application Security
SIEM
SOAR
Host Data Loss Prevention
HBSS
Virtualization Security
Advanced Managed SOC (Security Operations Center)
Identity and Access Management
Vulnerability Assessment
Email Security
Anti Phishing
Managed Compliance Services
GXP Compliance
IRAP Compliance
SAMA Compliance
MAS Compliance
RBI Compliance
GDPR Compliance
HITRUST Compliance
PCI-DSS Compliance
DevSecOps
SecOps
CI-CD Security
Application Security Testing
Leverage advanced cybersecurity and risk management across the IT stack
Introducing Self Healing Security:
Meet Cloud Engine Multi-award Winning SHOP Platform
Move over from traditional response management to predictive healing with with Cloud Engine Self-Healing Operations Platform (SHOP). Simply put, SHOP is a low code platform that integrates dozens of operations landscapes together into a single pane of glass while self-monitoring, predicting probable risks across the ecosystem and mitigating gaps even before the threats occur. Significantly reduce MTTD-MTTR to combat threats even before they occur.
Cloud Engine Defense in Depth
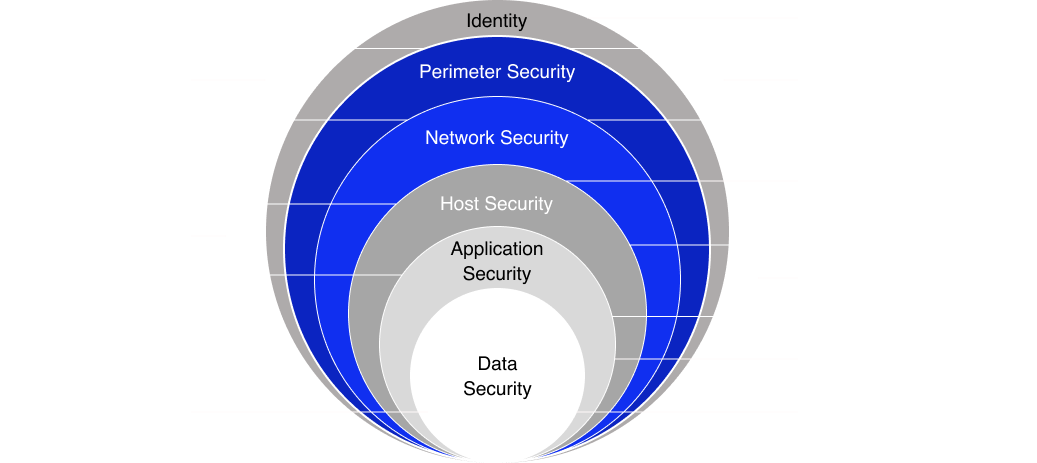
Proactive discovery of issues
Deep self-healing from risks
Real-time automated response
Service level optimization
Automated, Resilient Operations
Kickstart your Security Evolution:
Cloud Engine Security and Risk Assessment Workshop
Designed by Cloud Engine cybersecurity experts and threat management specialists, Security and Risk Assessment Workshop presents firms with current state risk analysis, discovers glaring loopholes, and delivers insightful recommendations on ways forward to evolve the organization’s cybersecurity posture. It’s the primary step before any transformation journey, helping firms effectively identify present needs and pinpoint strategic objectives for long-term future readiness.

 Current State Gap Analysis
Current State Gap Analysis Security and Industry Compliance Assessment
Security and Industry Compliance Assessment Tools Configuration Check and Mapping to Controls
Tools Configuration Check and Mapping to Controls Cloud Governance Check and Policy Assessment
Cloud Governance Check and Policy Assessment Cloud Native Tools Mapping
Cloud Native Tools Mapping Recommended Security Tools, Processes, and Technologies
Recommended Security Tools, Processes, and TechnologiesThe Difference:
Why Avail Cloud Engine Managed Cybersecurity Services?

→ Serving 4000+ enterprises including 60+ Fortune 500 organizations in 26 countries across Americas, Europe, Middle East, and APAC for 12+ years
→ Ensure fast alignment with digital banking innovations and trends
→ 25+ Centers of Excellence, 2000+ global cloud experts including certified security professionals
→ 3200 UTMs, 13000 HBSS, 800000 EPS
→ 7 Security frameworks, 40+ Security Controls
→ Powered by 24/7 SOC, NOC, Cybersecurity Incident and Response (CSIRT) teams
Let your digital transformation be risk-proofed and IT Operations be undisrupted.
FAQs
What are cyber security services?
Cybersecurity services or managed security services is a portfolio of offerings intended to provide end-to-end organizational protection. This includes data, servers, networks, applications, systems, platforms, virtual infra, assets, and end-point devices. The solution suite can be delivered on-premise, on cloud, or in a hybrid manner via a competent security services provider. With Cloud Engine cyber security services, avail intelligent threat management, predictive alerting to cyber threats, automated response management, advanced managed detection and response, security operations center management, end-point detection and management, preventive maintenance, and more. Avail an all-in-one intelligent cybersecurity program for your organization.
What are the 4 types of cyber attacks?
The cyber world is ridden with mal-practices. While enterprises certainly should adopt a no-threat policy irrespective of categories, some threats could have minimal impact yet some attacks could be devastating. Below are the common types of raging cyber threats in the e-world:
Malware – An umbrella term that stands for malicious software codes or programs including spyware, ransomware, viruses, and worms. A vulnerability in an IT system can expose the platform to these ‘devil algorithms’ that can steal important data, crash servers, block access to key functionalities, control the attack surface, or stay dormant and hidden for long continually harming the infrastructure
Phishing – A common mode of attack that impacts businesses and commoners alike, this entitles the reception of malicious emails or communications disguised as reputed ones. When user clicks on it or downloads an attached file, the malware enters the system to inflict havoc
Distributed Denial of Service Attack (DDoS) – Such an attack saturates servers, systems, databases, or networks with malicious or extra traffic to create a resource or bandwidth exhaustion. This consequently creates delays operations, stagnates IT processes, and increases the potential for threats
Zero-Day Vulnerability – As the name suggests, here attackers seize the period of time when an organization announces an IT or network vulnerability and takes a sufficient course of action. Often the most critical time spans for any organizational security, it takes advanced cybersecurity management partners or a dedicated cyber security solutions partner to efficiently mitigate the same.
Avail Cloud Engine end-to-end cyber security program or information security program to gain complete protection against all cyberattacks.
How do Cloud Services Work?
Cloud services specifically relate to distantly located, connected gargantuan computing infra being shared and accessed by multiple users globally via the web. Hence, firms only need an access device such as a computer and a stable internet connection to rent the provider’s computing infra, servers, datacenters basis operational needs thus eliminating the former’s hassles to maintain a full-fledged IT infrastructure on-premises. Clients accessing the cloud are only billed as per usage periodically.
